During an interview last week I was asked to define the difference between a Threat and a Risk using language that a non-technical CEO would understand. I gave a good answer and made it to the next round. And then I got to thinking—in my answer, I also talked about a third factor that should have been called out: Vulnerabilities.
Let’s start with some definitions:
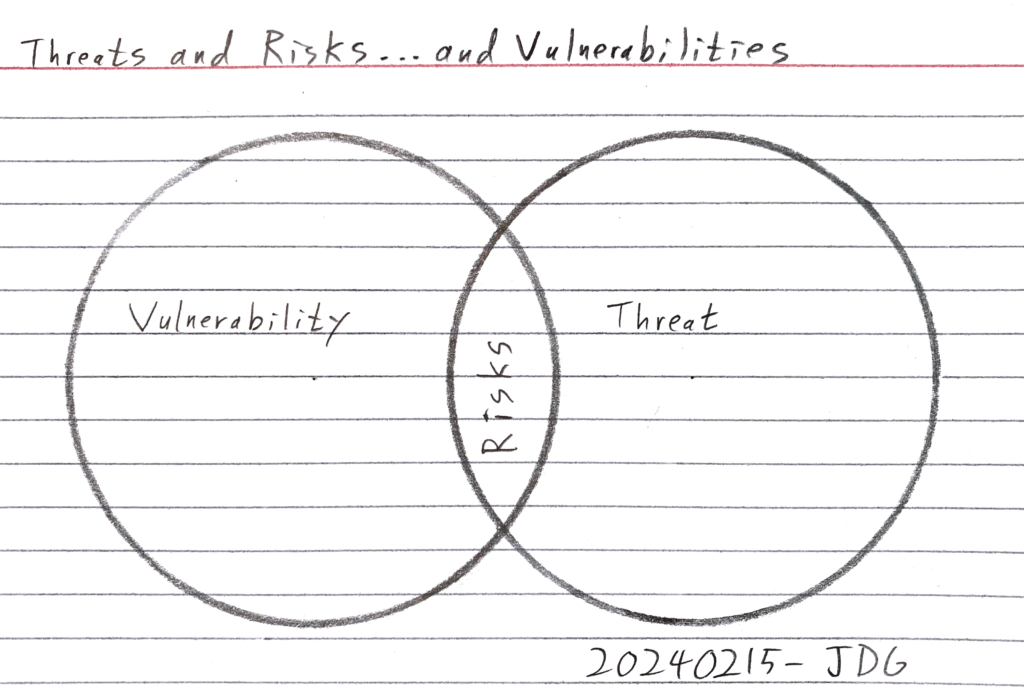
A vulnerability is a weakness in a system that exposes the system to a threat.
A threat is anything that could exploit a vulnerability.
A risk is the likelihood of a negative event and the likely impact.
Risks are found at the intersection between vulnerabilities and threats.
The CEO’s password example
A CEO’s password is vulnerable when it’s short and simple. The threat is that someone (a threat actor) will figure out the password and use it against the CEO. There is a risk that1 the threat actor will exploit the vulnerability (the short and simple password), coupled with the subsequent business impact (loss of data confidentiality, loss of data integrity).
What are some controls that we could put into place to reduce the risk? We can manage2 the vulnerability by requiring complex, long passwords and MFA, reducing the probability of the CEO’s account being compromised (the negative event) by the threat actor. We can reduce the impact by ensuring that the CEO the correct access to systems and data needed to perform the job.
A non-cyber example
As I look out my window today, it’s snowing, as it should in mid-February.3 In this example, a threat might be a massive lake-effect snowstorm. Some vulnerabilities might be a refrigerator with no bread or milk, an inadequate heating system and an aging electrical connection. There is a risk that a massive lake-effect storm could bury us under three feet of snow (negative event) causing us to suffer harm (negative impact) by starving, getting very cold or losing power.
As an experienced midwesterner living in my particular zip code, I have implemented some controls to remove some of my vulnerabilities (and reduce my risk) by stocking up on flour, yeast and milk, having alternate heating (and cooking sources) and keeping a supply of flashlights, batteries and candles. That’s an example of how I’ve chosen to manage this risk.
Wrapping up
Threats operate against one or more vulnerabilities. Vulnerabilities are weaknesses that expose us to threats. But a vulnerability itself isn’t a risk. Risk is the probability of something negative happening, coupled with its impact. Some low probability and low impact risks may not be worth the trouble to reduce or eliminate. And some risks that are low probability but insanely high impact may warrant a completely different response.
But that’s a different post for another day.
- This is a useful phrase to employ and helps me think about such things: “There is a risk that . . . (some negative outcome may take place).” ↩︎
- I feel uncomfortable claiming that this vulnerability can be eliminated or removed. ↩︎
- Since we live on the edge of Lake Erie’s snowbelt. ↩︎
References:
Maymi, F., & Harris, S. (2019). CISSP all-in-one exam guide (8th ed., Ser. All-in-one). McGraw-Hill Education.

