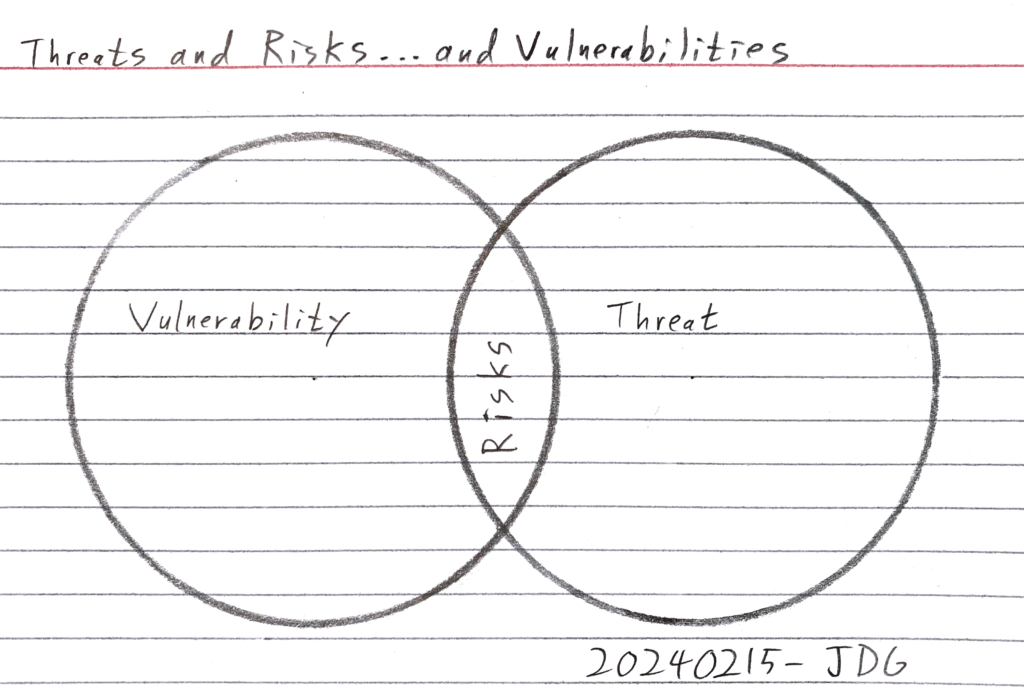
Most of the vulnerability management programs I’ve encountered suffered from analysis paralysis—the infosec team had reams of data (or multiple spreadsheets) on their vulnerabilities but couldn’t make progress because they couldn’t decide where to start.
Questions I frequently hear include:
- What’s the biggest vulnerability (AKA high-risk)?
- What vulnerability hits the most systems?
- What vulnerabilities are most easily exploited?
- What vulnerabilities impact the highest critical business system(s) the most?
Those are all excellent questions and they assume a level of maturity that an analysis paralysis-level organization hasn’t reached yet. Maybe you haven’t completed (or started) a BIA project to determine your critical business systems. Maybe you’re still working on your device inventory. Maybe you don’t know how to define “biggest” yet.
Continue reading